I admit that setting up Hypertext Transfer Protocol Secure (HTTPS) isn’t as easy as it should be. But there’s no reason why something a massive as the federal government, especially when you consider the fact that it can steal as much money as it wants, can’t properly setup HTTPS. But it can’t.
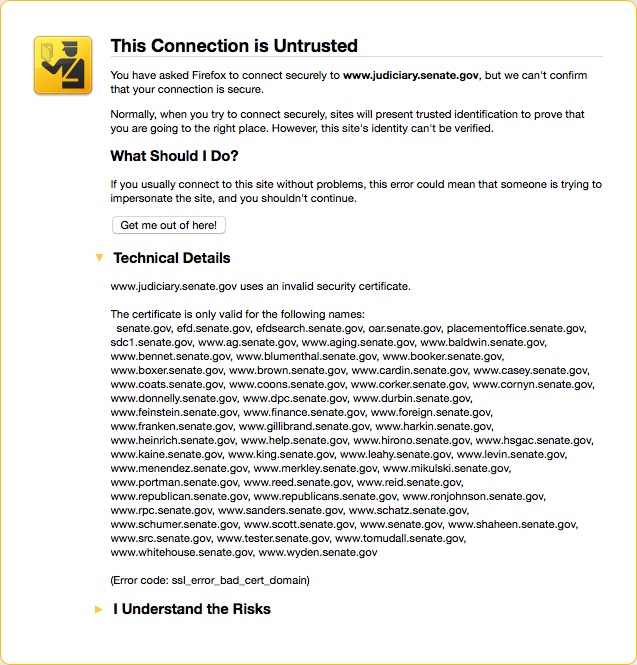
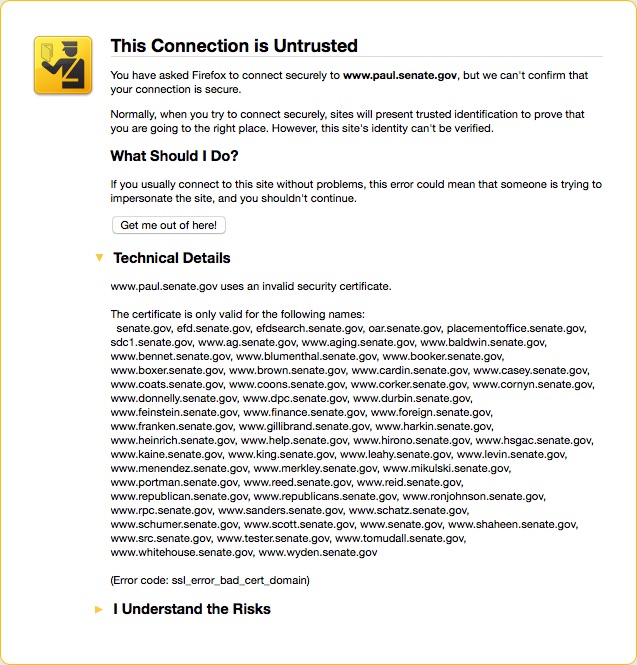
I use HTTPS Everywhere to force as many sites as humanly possible over HTTPS instead of HTTP. Usually this works very well but sometimes a site isn’t properly setup and my user experience goes south. The Senate website is one of the sites that provides a suboptimal user experience. Take a look at these two exceptions I received when trying to access information on the Senate’s website:
The thing to note is that the web server is setup to give each senator their own subdomain. This requires the certificate to contain each individual subdomain. As you can see by the errors I received the certificate doesn’t contain the subdomain for the Committee of the Judiciary or Rand Paul. There are two things to take away from this.
First, the Senate’s web server is setup in a very fragile way. Instead of creating a separate subdomain for each senator it would have been much smarter to create a separate subdirectory for each senator. The only difference that would make for the user is they would have to type https://www.senate.gov/paul instead of https://www.paul.senate.gov. Since no subdomains would be needed the certificate wouldn’t have to contain the name of every senator and Senate committee.
Second, whoever is in charge of maintaining the certificate for the Senate’s web server is incompetent. Since each senator has a separate subdomain the certificate should be renewed after every election with the subdomains of the new senators added and the subdomains of the old senators removed. Likewise, the certificate should be renewed every time a new Senate committee is created or an old one is retired. That would allow users to securely connect to each Senator’s website.
In all likelihood this setup is the result of the server originally being created without any consideration given to security. When security became a concern the system was probably patched in the all too common “good enough for government work” manner instead of being redesigned properly to reflect the new requirements. And since there is almost no accountability for government employees nobody tasked with maintaining the server probably saw fit to periodically verify that the certificate is valid for every available subdomain.
I would argue that this is yet another example of the government’s poor security practice that should have everybody worried about the data it collects.