I received a comment from Sonia on my post detailing Bruce Schneier’s tips for protecting yourself from the National Security Agency (NSA):
This kind of endeavor only works is everybody does it, otherwise is useless. Also inviting laymen to “learn” reveals how much you underestimate the fact that being a programmer gives you all the mental models you need.
Those people who “learn” will only end up compromising their own security under the impression that they are doing something secure.
Although I addressed these concerns in a reply I wanted to write a post because I feel what I’m about to say is relevant to anybody interested in computer security.
In another comment Sonia mentioned she (I’m assuming Sonia is female based on name, this being the Internet I could be incorrect) is a Ph.D. That being the case, I can see where her views on this subject come from. Oftentimes those of us who have been involved in the computer field for some time fall victim to two issues. First, we develop a form of elitist attitude that causes us to think of ourselves as somehow superior to non-techie people. Second, we forget about the early days when we knew little about computers. I’ve fallen victim to these issues before and I believe Sonia has fallen victim to them in her comment.
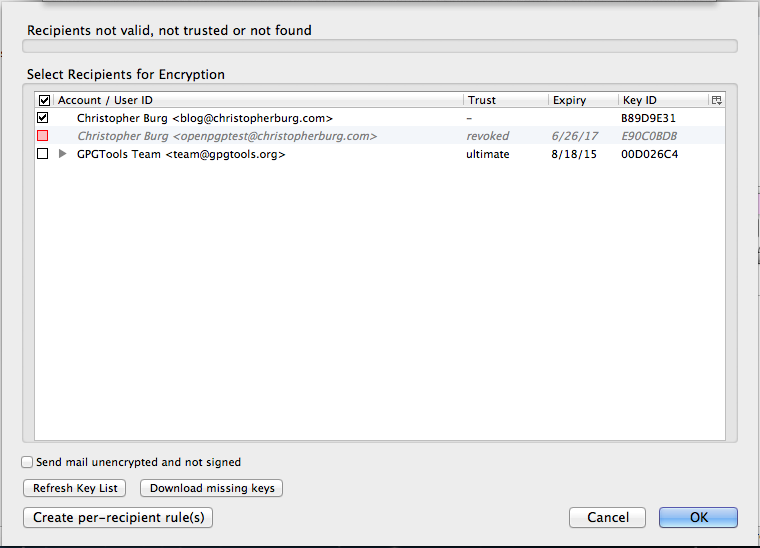
She does make a very important point. When you first dive into computer security you’re going to make mistakes. This is a problem all people face when learning something new. Just because you know how to utilize OpenPGP to encrypt your e-mail doesn’t mean you fully grasp underlying concepts such as private key security, the inability to know whether or not a closed system is secure, the value of a proper security audit, or the potential issue of generating keypairs on a system that lacks a true cryptographically secure pseudorandom number generator. All of these things, and more, play a part in OpenPGP and computer security.
You know what? That’s OK. You don’t need to know everything right away. Everybody has to start from the beginning. I didn’t become a computer programmer or system administrator overnight. I wasn’t blessed with the innate knowledge required to operate and manage an OpenBSD system. At one point I had no idea what Postfix was, let alone how to run and maintain a Postfix server. The difference between C and C++ were unknown to me back in the day. All of this knowledge came with due time. I’ve invested years into learning what I now know about computers and will likely invest a lifetime into learning more. When I started to program I made countless amateur mistakes. That didn’t discourage me because I learned from those mistakes. I’m happy to report that I’m still learning from my mistakes today.
Learning how to use the tools necessary to keep yourself safe online isn’t going to happen overnight. You’re going to make mistakes. Those mistakes will compromise your security. But you will learn from those mistakes and you will become more secure because of it.
Computer security isn’t an all-or-nothing thing. Even if you don’t practice proper private key security or generate an easily determinable keypair because your system lacks a secure pseudorandom number generator you’re more secure by using OpenPGP or Off-the-Record Messaging than not. Every encrypted communication requires potential spies to throw time and resources at decrypting it just to find out what’s in it. Simply put, every encrypted communication helps defend everybody’s privacy. As the number of encrypted communications increase potential spies must either prioritize the computing resources available to them or invest other resources into more computing resources.