As if spying on our telephone conversations wasn’t bad enough another disturbing fact was revealed about the National Security Agency’s (NSA) vast spying operations. Although we all suspected that the NSA had access to the databases of the largest technology companies in Silicon Valley we now have proof:
A top-secret surveillance program gives the National Security Agency surreptitious access to customer information held by Microsoft, Yahoo, Apple, Google, Facebook, and other Internet companies, according to a pair of new reports.
The program, code-named PRISM, reportedly allows NSA analysts to peruse exabytes of confidential user data held by Silicon Valley firms by typing in search terms. PRISM reports have been used in 1,477 items in President Obama’s daily briefing last year, according to an internal presentation to the NSA’s Signals Intelligence Directorate obtained by the Washington Post and the Guardian newspapers.
This afternoon’s disclosure of PRISM follows another report yesterday that revealed the existence of another top-secret NSA program that vacuums up records of millions of phone calls made inside the United States.
What does this mean? A lot. Effectively the NSA has access to every e-mail sent to or from Microsoft, Yahoo, and Google’s services. It also means that the NSA has access to everything you’ve posted on Facebook including comments, pictures, and private messages regardless of your privacy settings. Microsoft, Yahoo, and Google searches are also obtainable by the NSA. In other words, anything you’ve ever send to or accessed from the servers of the involved technology companies is at the fingertips of the NSA.
Concern about this very thing is what lead me to move all of my needed online services to my personal server. My e-mail, calendaring, address booking, Virtual Private Network (VPN), and websites are all hosted on a server physically located in my dwelling. Hosting all of your own services can be a pain in the butt at times but it’s the only way to have any reasonable assurance that your confidential information remains confidential. I recommend everybody buy a domain name and move their online services away from major technology companies and onto their own services. If you’re not sure how to do that then it’s time to learn and I will gladly help anybody want asks for it.
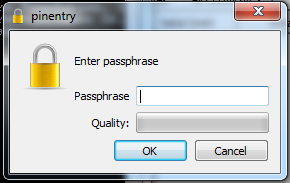
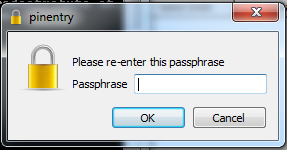
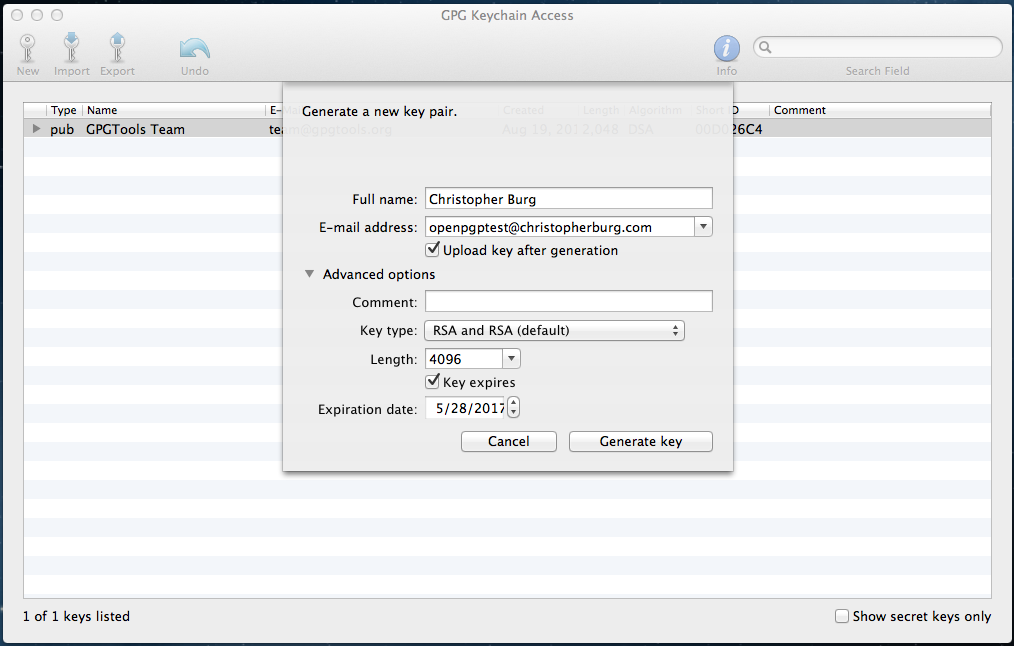
If you can’t pull yourself away from third-party services then you need to encrypt everything. I’ve written a few tutorials that explain how to encrypt e-mail using OpenPGP. As of this writing the tutorial for OS X is completed, the first part of the Windows tutorial is completed, the first part of the Linux tutorial will be posted later today, and the tutorial explaining how to use Thunderbird and Enigmail to send and receive encrypted e-mails will be posted in the near future. When the Cyber Intelligence Sharing and Protection Act (CISPA) was being debated in Congress I wrote a short guide that explained a few technologies that could be used to avoid the state’s prying eyes, learn how to use them (I will write detailed guides at some point).
To quote a famous phrase, shit just got real.